Configuration¶
Instance Certificate¶
The OPC UA connector installs a self-signed certifcate that identifies this specific installation of the connector. OPC UA servers need to trust this certificate before a data exchange can occur. The certificate is different for each installation and is sent to OPC UA servers when the connector connects. The self-signed certificate is issued with a validity period of three years.
View instance certificate¶
Goto the configuration node in the navigation tree to view the instance certificate. The instance certificate is always trusted by the OPC UA connector itself.
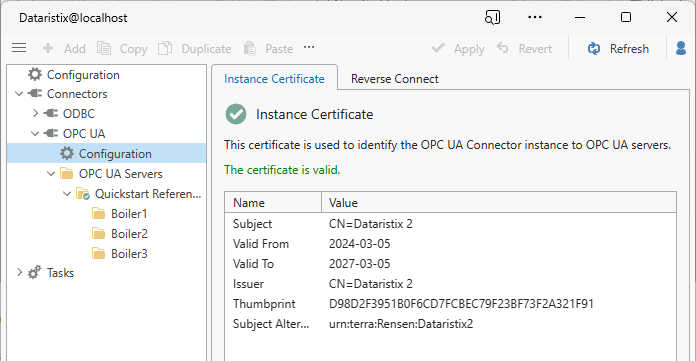
Configure instance certificate¶
You can renew the certificate, import a different certificate as a replacement, or export the currently used certificate by clicking on the corresponding toolbar button. Be careful when renewing or replacing a certificate because OPC UA servers that trust the old certificate will not recognize the new certificate. A warning is shown before renewal or import of a certificate and you have to confirm that you wish to proceed.
Issuer and Intermediate Certificates¶
If your OPC UA server certificates use intermediate or issuer certificates in their chain then you may need to add these issuer or intermediate certificates to the OPC UA Connector’s certificate store manually. On Windows, the certificate store is located at:
C:\ProgramData\Rensen\Dataristix 3\modules\OPC UA Connector\pki
Containerized applications store certificates in OPC UA Connector subfolder within the “dataristix-secret” folder.
Place issuer certificates into an “issuer” subfolder and trusted intermediate certificates into the “trusted” subfolder. Do not remove any OPC UA server certificates present there since these are automatically managed by the OPC UA Connector. You will need to be an administrator to access the PKI folder.
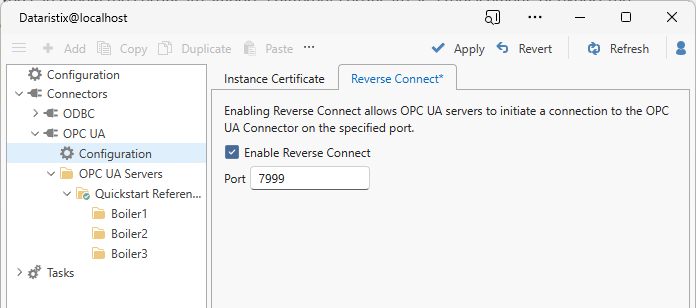
Reverse Connect¶
Enable “Reverse Connect” to allow OPC UA servers to connect to the OPC UA Connector using the given port.
If the specified port is 7999 (for example) and the OPC UA Connector runs on a computer with host name
“hostname” then the OPC UA server should be configured to connect to client endpoint opc.tcp://hostname:7999.
Since the OPC UA server now initiates the “reverse” connection, the OPC UA server may run behind a firewall allowing outbound connections only. The client computer (OPC UA Connector computer) needs to allow incoming connections on the given port.