Projects¶
Export Project¶
To save all settings, including tasks, connector topics and connector tags, select “Export Project” from the “File” menu.
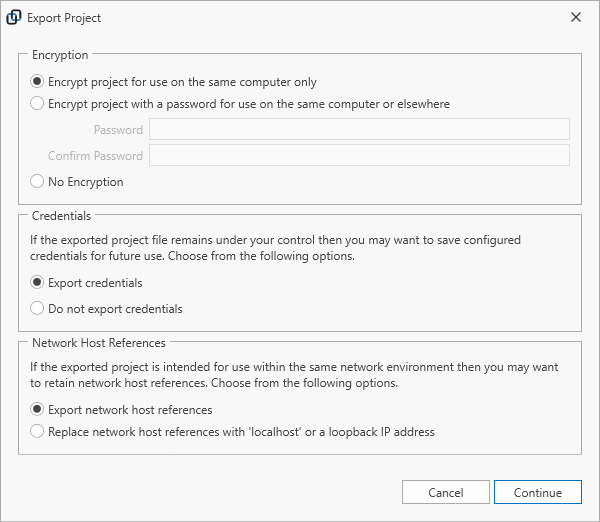
The following export options are available.
Encryption Options¶
- Encrypt project for use on the same computer only
- The project file is encrypted with a computer specific encryption key and the project file can be imported on the same computer only.
- Encrypt project with a password for use on the same computer or elsewhere
- The project file is encrypted with a password and can be imported on any computer after entering the correct password.
- No Encryption
- The project file stores information in plain text. If this option is selected then credentials cannot be exported.
Credentials Option¶
- Export credentials
- Configured passwords or access keys will be exported. This option is available for encrypted projects.
- Do not export credentials
- Configured passwords or access keys will be removed from the exported project and need to be re-entered after import.
Network Host References Option¶
- Export network host references
- If selected, then all network host references will be retained in the exported project. Use this option if the project is intended for import onto a computer within the same network environment.
- Replace network host references with ‘localhost’ or a loopback IP address
- If selected, then all network host references are replaced. Use this option if the project is intended for import onto a computer within a different network environment. Host references need to be updated after project import to reflect the new network environment.
Import Project¶
To load all settings, including tasks, connector topics and connector tags, select “Import Project” from the “File” menu and open a previously exported project file. For the import to succeed, connector modules and processor modules that the project requires must be installed. Installed software modules must not be older than the software modules used when the project was exported.
Warning
Importing a project will overwrite all currently configured tasks, connector topics and processor settings.
Important
To install an instance of Dataristix on a new computer as a replacement, ensure that not only a previously exported project is re-loaded, but also restore previously backed up certificates if trust relationships must be retained. Please see details below.
Use of certificates¶
Various Dataristix connectors use certificates for identification. These certificates do not form part of the project but remain in place when projects are loaded or when a new project is started. This means:
- The OPC UA connector retains the OPC UA client identity that is trusted by OPC UA servers, and you do not need to trust the Dataristix client again on the OPC Server side.
- For the MQTT connector, the broker’s certificate authority and server certificates remain the same and MQTT clients continue to trust the broker.
Some certificates may become inaccessible when loading a project or when starting a new project:
- Dataristix MQTT client certificates may become inaccessible because the MQTT clients present in the new project may be different from the previous MQTT clients. However, previously used certificates are cached, and if the new project contains MQTT clients with references to a previously cached certificate, then the previous MQTT client certificate will be restored. Generally, project iterations using the same MQTT clients retain their certificates and trust relationships.
- REST client certificates may become inaccessible because the REST clients present in the new project may be different from the previous REST clients. Again, if the new project contains REST clients with references to a previously cached certificate, then the previous REST client certificate will be restored, and project iterations using the same REST clients retain their certificates.
In short, on the same computer, certificates and trust relationships are retained across different projects. Restoring a Dataristix instance on a different computer requires further consideration.
Certificate backup strategies¶
It is important to note that certificates that could potentially contain a private key are not included in an exported project; the saved project file does not contain the OPC UA client instance certificate, the MQTT certificate authority certificate, the MQTT server certificate, or the REST client certificates. Therefore, a new installation of Dataristix on another computer will use different certificates even after loading a previously saved project. Without precautions, trust relationships established by the original certificates would need to be restored. That means, OPC UA servers would need to trust the new Dataristix instance, MQTT clients would need to trust the new Dataristix broker certificates, and REST servers that require trusted client certificates would need to be configured to trust the new Dataristix REST client certificates.
For disaster recovery, the best option is therefore, to backup relevant Dataristix certificates including private keys, so that previous trust relationships can be restored if required. This may be achieved in one of the following ways:
Using file history or other backup mechanism for the computer where Dataristix is installed. This strategy would aim at restoring the entire machine state to a state where the correct certificates are present in the file system.
Keeping a backup of the PKI folders (Public Key Infrastructure folders) of the connectors that use certificates. These ‘pki’ folders are found in the respective “Program Data” folder of the connector:
C:\ProgramData\Rensen\Dataristix\modules\MQTT ConnectorC:\ProgramData\Rensen\Dataristix\modules\OPC UA ConnectorC:\ProgramData\Rensen\Dataristix\modules\REST ConnectorPKI folders are protected, and you would need to be a system administrator to gain access to these folders. Keep backups of the contained certificate files. To restore the PKI files, locate the PKI folder on the new system, delete any existing content, and copy all backed up files contained in the previous PKI folder. Finally, restart the relevant Dataristix connector services using the Windows Services panel.
If you have used “openssl” to create certificates and imported these certificates into Dataristix (instead of using certificates generated by Dataristix) then you may already have a set of certificate files and private keys; simply ensure that these files are kept in a safe place, in case you need them to configure another Dataristix instance.
Note that exporting a certificate in Dataristix does not export the private key. If a private key is needed for operations (for the MQTT broker server certificate, the OPC UA application instance certificate, or possibly the REST client certificate), then the exported certificates cannot be reimported since they are missing the private key. The MQTT broker’s certificate authority certificate can be used without a private key, but without private key, it cannot be used to issue device certificates.